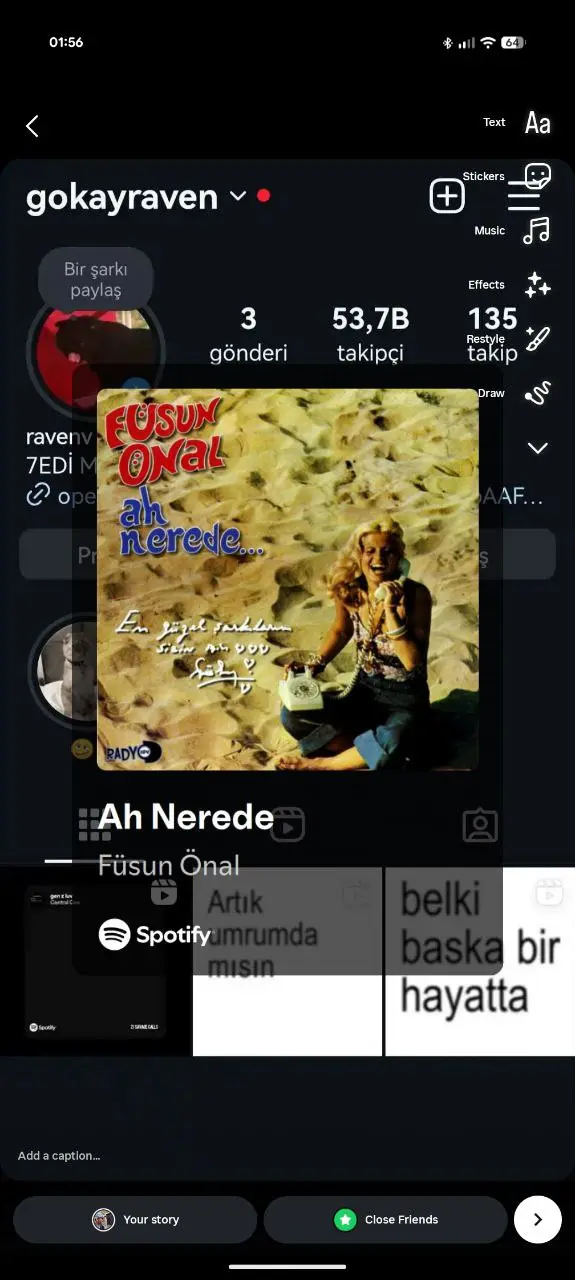
When Spotify’s Share-to-Instagram Flow Turns Into a Free Billboard
Earlier this week, I tried sharing a song on Instagram Stories “Füsun Önal – Ah Nerede“, the 2004 release. Spotify → Share → Instagram. Something we all do a thousand times. But instead of the album cover, Instagram opened with a completely unrelated person’s Instagram profile screenshot. Not mine. Not Spotify’s. Someone else’s — essentially … Read more