When working with AWS (Amazon Web Services), securing your infrastructure is paramount. One of the most common security practices is to restrict access to your private subnets by avoiding the use of 0.0.0.0/0, which represents all IP addresses globally. While this enhances security, it can also present challenges when your applications and services need to interact with various AWS services. This article will guide you on how to securely access AWS services from private subnets without exposing your resources to the public internet.
In this guide, we’ll explore different methods to achieve this, dive into specific AWS services, and provide practical examples to help you implement these strategies. Whether you’re a seasoned AWS user or just starting out, this guide will equip you with the knowledge to enhance the security and functionality of your cloud infrastructure.
Why Avoid 0.0.0.0/0?
The IP address 0.0.0.0/0 is shorthand for “anywhere.” When used in security groups or network access controls, it allows access from any IP address in the world. While this might be necessary in some scenarios, it’s generally considered risky because it exposes your resources to potential attacks. By restricting access to specific IP ranges, you can significantly reduce the attack surface of your infrastructure.
Strategies to Access AWS Services Without 0.0.0.0/0
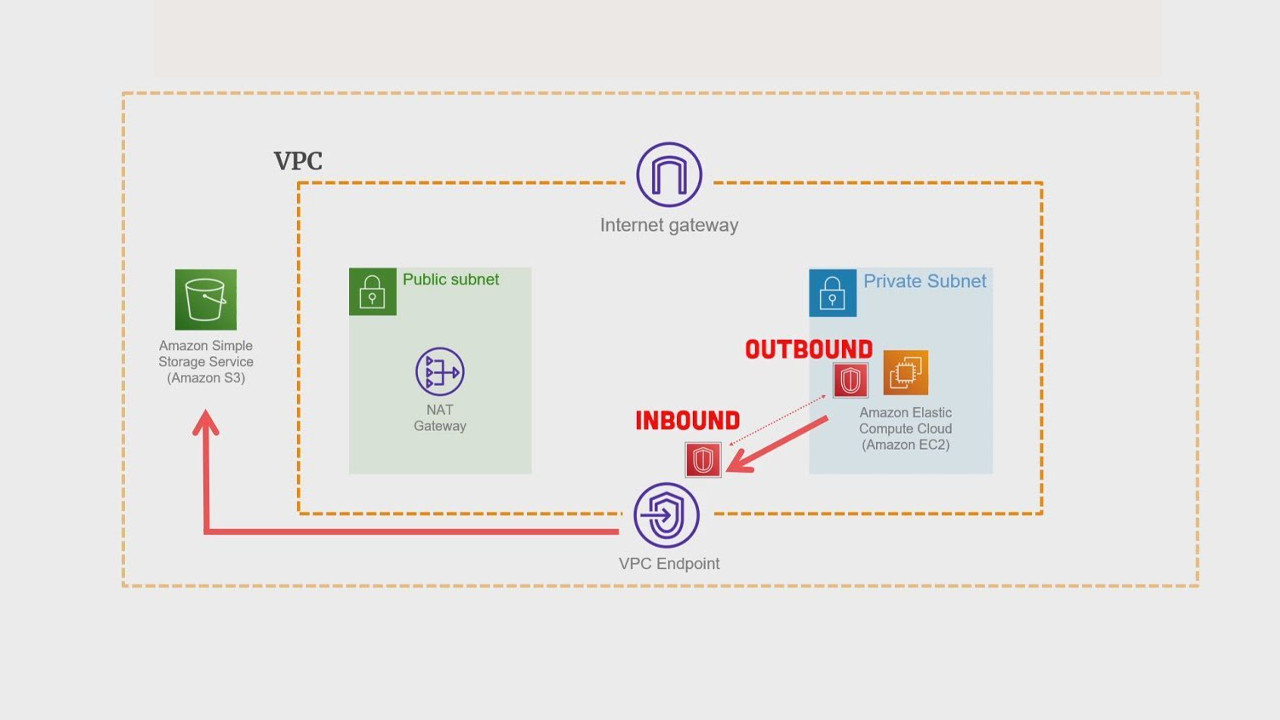
1. Using VPC Endpoints
AWS VPC (Virtual Private Cloud) Endpoints allow you to privately connect your VPC to supported AWS services without requiring an Internet Gateway, NAT device, VPN connection, or AWS Direct Connect. Traffic between your VPC and AWS services does not leave the Amazon network, providing enhanced security and performance.
There are two types of VPC Endpoints:
- Interface Endpoints: These are powered by AWS PrivateLink and are used to access services such as EC2, KMS, CloudWatch, and more. They create an elastic network interface in your subnet with a private IP address, enabling communication with the AWS service.
- Gateway Endpoints: These are used to access Amazon S3 and DynamoDB. They act as a target for a route in your route table, directing traffic for the specified service to the endpoint.
Example Services:
- Amazon S3
- Amazon DynamoDB
- Amazon EC2
- AWS Systems Manager
- Amazon SNS
- Amazon SQS
2. NAT Gateways
A NAT (Network Address Translation) Gateway is a managed service that allows instances in a private subnet to connect to the internet or other AWS services, but prevents the internet from initiating a connection with those instances. Unlike an Internet Gateway, a NAT Gateway does not allow inbound traffic from the internet, making it a safer option for accessing public AWS services from a private subnet.
NAT Gateways are highly available within a single Availability Zone and can be scaled to meet your traffic demands. When deploying a NAT Gateway, it’s recommended to set it up in a public subnet and configure the route tables of your private subnets to use the NAT Gateway for internet-bound traffic.
Example Services:
- Amazon EC2
- Amazon RDS
- Amazon Redshift
- AWS Lambda
- Amazon ElastiCache
3. AWS Transit Gateway
AWS Transit Gateway enables you to connect your VPCs, on-premises networks, and AWS services through a central hub. It acts as a highly scalable cloud router that simplifies network architecture and ensures secure, scalable, and managed connections between your resources.
Transit Gateway allows you to route traffic between your VPCs and on-premises networks without needing a direct internet connection. This is particularly useful for large-scale architectures where multiple VPCs or regions need to interact securely.
Example Services:
- Amazon VPC
- AWS Direct Connect
- AWS Site-to-Site VPN
- Amazon S3 (via VPC Endpoints)
- Amazon DynamoDB (via VPC Endpoints)
4. AWS Direct Connect
AWS Direct Connect provides a dedicated network connection from your premises to AWS. It bypasses the internet entirely, offering a more secure and reliable way to connect your private subnets to AWS services. Direct Connect is often used in hybrid cloud architectures where on-premises resources need to interact with AWS services securely.
By using Direct Connect, you can route traffic from your private subnet to AWS services via a private connection, ensuring that your data remains within the AWS network and reducing exposure to external threats.
Example Services:
- Amazon EC2
- Amazon RDS
- AWS Lambda
- Amazon S3
- Amazon CloudFront
5. AWS PrivateLink
AWS PrivateLink allows you to securely access services hosted on AWS in a private and highly available manner. It eliminates the need for a NAT device, Internet Gateway, or VPN connection. PrivateLink establishes a direct connection between your VPC and the AWS service through an interface endpoint.
This service is particularly useful for accessing third-party SaaS applications or custom services hosted within AWS. With PrivateLink, traffic remains within the AWS network, further securing your interactions with external services.
Example Services:
- Amazon CloudWatch
- AWS Secrets Manager
- AWS CodeBuild
- Amazon ECR
- Amazon Kinesis
6. VPC Peering
VPC Peering allows you to connect one VPC with another, enabling instances in either VPC to communicate as if they were within the same network. VPC Peering is a simple, one-to-one connection between VPCs, which can be within the same AWS account or different accounts.
While VPC Peering does not inherently provide access to AWS services, it can be combined with other methods (such as VPC Endpoints) to allow instances in a private subnet to securely access services hosted in another VPC.
Example Services:
- Amazon EC2
- Amazon RDS
- Amazon S3 (via VPC Endpoints)
- Amazon DynamoDB (via VPC Endpoints)
- Amazon EKS
7. Elastic Load Balancers (ELB)
Elastic Load Balancers (ELB) distribute incoming traffic across multiple targets, such as EC2 instances, containers, or IP addresses, in one or more Availability Zones. By placing an ELB in a private subnet and using it to route traffic to your resources, you can securely expose your services to other AWS services without direct internet exposure.
For example, an Application Load Balancer (ALB) can route traffic from an interface endpoint to your EC2 instances, while a Network Load Balancer (NLB) can manage traffic from your on-premises resources to AWS services.
Example Services:
- Amazon EC2
- Amazon ECS
- AWS Fargate
- AWS Lambda
- Amazon RDS
8. AWS Systems Manager (SSM)
AWS Systems Manager provides a secure, scalable way to manage your AWS resources. With Systems Manager, you can remotely access and manage your EC2 instances and other resources in private subnets without requiring a direct internet connection.
SSM Session Manager, a feature of Systems Manager, allows you to securely connect to your instances without the need for SSH or RDP access, further reducing the need for 0.0.0.0/0. It also integrates with IAM, providing fine-grained access control.
Example Services:
- Amazon EC2
- Amazon RDS
- AWS Lambda
- Amazon CloudWatch
- AWS Config
AWS Services and Their Private Access Solutions
Let’s take a closer look at how you can securely access various AWS services from private subnets using the strategies mentioned above:
1. Amazon S3
- Access Method: Gateway VPC Endpoint
- Description: You can create a Gateway VPC Endpoint for Amazon S3, allowing your instances in private subnets to access S3 buckets without exposing your resources to the internet.
2. Amazon DynamoDB
- Access Method: Gateway VPC Endpoint
- Description: Similar to S3, DynamoDB can be accessed securely from private subnets by creating a Gateway VPC Endpoint.
3. Amazon EC2
- Access Method: NAT Gateway, VPC Peering, SSM
- Description: EC2 instances in private subnets can access public AWS services through a NAT Gateway or connect with other VPCs via VPC Peering.
4. Amazon RDS
- Access Method: NAT Gateway, VPC Peering
- Description: You can access your RDS instances from private subnets using a NAT Gateway or VPC Peering.
5. Amazon Redshift
- Access Method: NAT Gateway, Interface VPC Endpoint
- Description: Redshift clusters can be accessed via NAT Gateways or Interface VPC Endpoints, ensuring private subnet resources can interact securely.
6. AWS Lambda
- Access Method: VPC Endpoints, SSM
- Description: Lambda functions can access private subnets via VPC Endpoints, and you can manage them securely with AWS Systems Manager.
7. Amazon ElastiCache
- Access Method: NAT Gateway, VPC Peering
- Description: ElastiCache can be accessed from private subnets using NAT Gateways or VPC Peering.
8. Amazon CloudWatch
- Access Method: Interface VPC Endpoint, SSM
- Description: Monitor your resources in private subnets by accessing CloudWatch through an Interface VPC Endpoint or managing them with SSM.
9. AWS Secrets Manager
- Access Method: Interface VPC Endpoint, PrivateLink
- Description: Securely store and retrieve secrets from your private subnets using an Interface VPC Endpoint or PrivateLink.
10. Amazon ECR
- Access Method: Interface VPC Endpoint, NAT Gateway
- Description: Access container images stored in ECR from private subnets using Interface VPC Endpoints or NAT Gateways.
11. Amazon SQS
- Access Method: Interface VPC Endpoint, NAT Gateway
- Description: Securely send and receive messages from SQS using Interface VPC Endpoints or NAT Gateways.
12. Amazon SNS
- Access Method: Interface VPC Endpoint, NAT Gateway
- Description: Send notifications to SNS from private subnets through Interface VPC Endpoints or NAT Gateways.
13. Amazon Kinesis
- Access Method: Interface VPC Endpoint, PrivateLink
- Description: Securely process streaming data using Kinesis in private subnets via Interface VPC Endpoints or PrivateLink.
14. AWS CodeBuild
- Access Method: Interface VPC Endpoint, PrivateLink
- Description: Run your build processes in private subnets by accessing CodeBuild with Interface VPC Endpoints or PrivateLink.
15. AWS CloudFormation
- Access Method: Interface VPC Endpoint, NAT Gateway
- Description: Deploy and manage your infrastructure using CloudFormation in private subnets via Interface VPC Endpoints or NAT Gateways.
16. AWS Step Functions
- Access Method: Interface VPC Endpoint, NAT Gateway
- Description: Orchestrate workflows in private subnets by accessing Step Functions through Interface VPC Endpoints or NAT Gateways.
17. Amazon EFS
- Access Method: VPC Peering, PrivateLink
- Description: Share files between private subnets securely using EFS with VPC Peering or PrivateLink.
Conclusion
Securing access to AWS services from private subnets is essential for maintaining the security and integrity of your cloud environment. By avoiding the use of 0.0.0.0/0 and leveraging the various AWS networking features like VPC Endpoints, NAT Gateways, and AWS Direct Connect, you can ensure that your infrastructure remains secure while still being able to interact with necessary AWS services.
Understanding and implementing these strategies will not only enhance the security of your AWS environment but also improve performance and reliability. With the knowledge gained from this guide, you can confidently build and manage a robust cloud architecture that meets the highest security standards.
By integrating these methods into your architecture, you’ll be well on your way to creating a secure, efficient, and scalable AWS environment that minimizes exposure to the public internet while maximizing functionality.
For more detailed instructions on implementing these methods, refer to the official AWS documentation or consult with an AWS Solutions Architect to tailor the solutions to your specific needs.