As a beginner in MySQL, you might encounter an error message that reads “ERROR 1819…
Tag: security

The AWS Well-Architected Framework: A Key to Cloud Success
Why It’s Important, Why You Need It, and Its Key Role in Your Cloud Journey…

Secure Your Media Files by Removing Metadata with AWS Lambda
In today’s digital world, images and videos often contain metadata that reveals a surprising amount…

CORS in Nginx: Configuration Guide for Enhanced Security
Cross-Origin Resource Sharing (CORS) is a crucial mechanism for enabling secure communication between web servers…
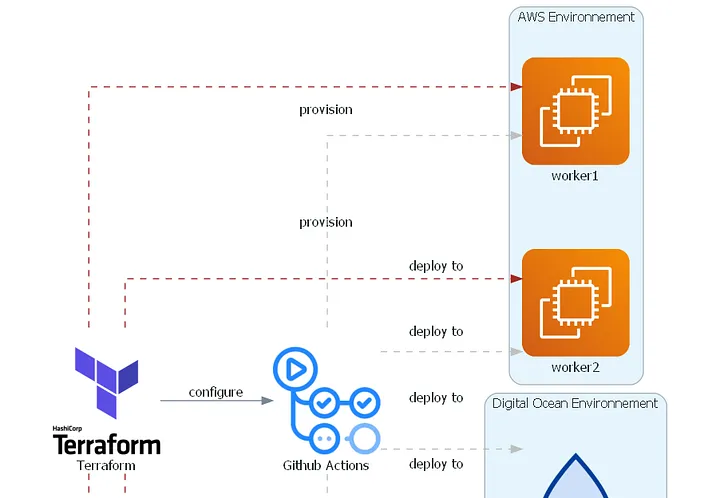
Creating SSH Keys for Secure Access to AWS EC2 Instances with Terraform
When working with cloud infrastructure, security is of utmost importance. One critical aspect of security…
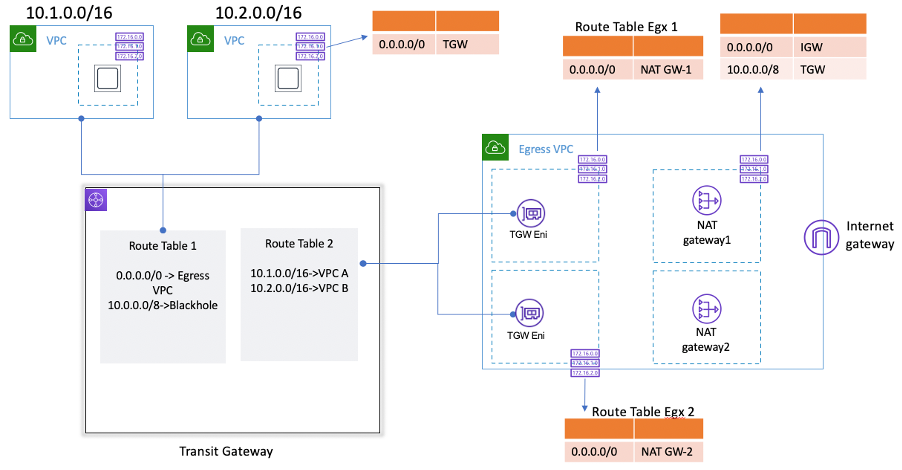
What is an Egress only internet gateways in AWS?
Amazon Web Services (AWS) is one of the leading cloud computing platforms, providing a variety…
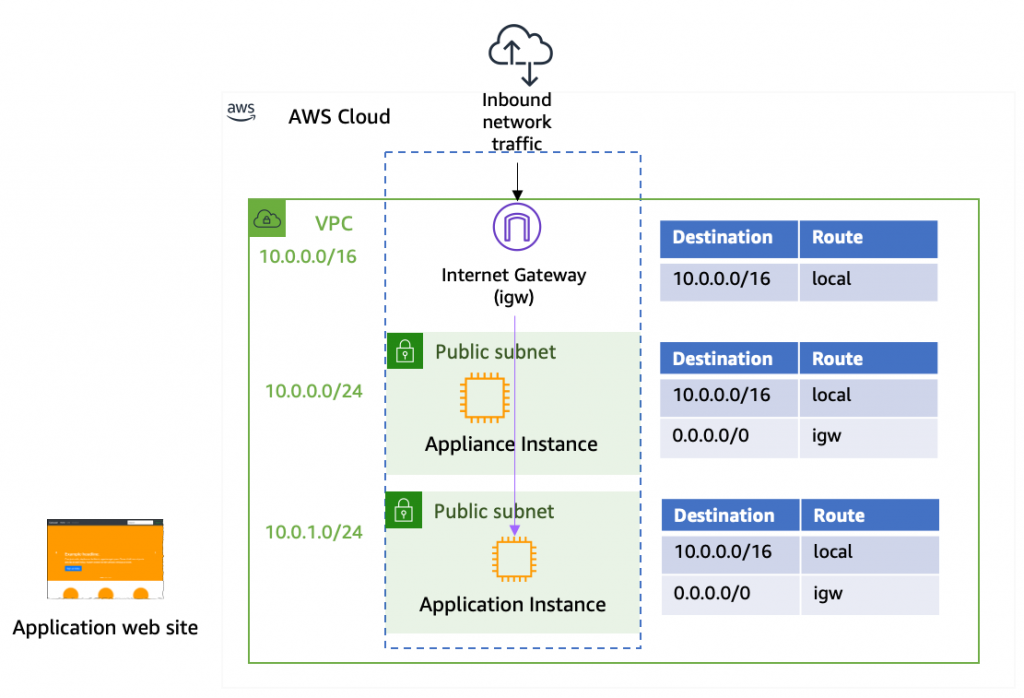
What are Route Tables on AWS VPC?
Route tables in Amazon Web Services (AWS) are used to determine how traffic is directed…

Create an S3 Bucket and Set a Policy via CLI
I really like to use CLI commands and it’s my daily routine. Today, I’ll tell…

Automate Let’s Encrypt SSL on AWS Application Load Balancer
Most of the time, we don’t need anything except AWS Certificate Manager (ACM) but in…
