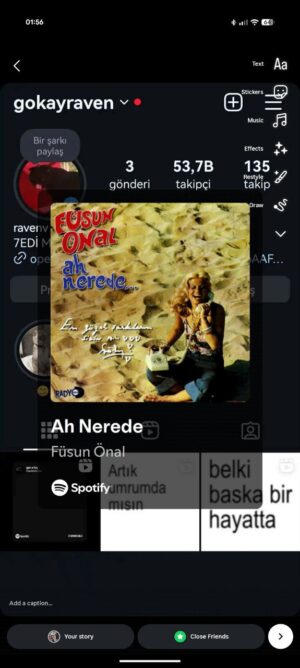
Earlier this week, I tried sharing a song on Instagram Stories “Füsun Önal – Ah Nerede“, the 2004 release.
Spotify → Share → Instagram. Something we all do a thousand times.
But instead of the album cover, Instagram opened with a completely unrelated person’s Instagram profile screenshot. Not mine. Not Spotify’s. Someone else’s essentially a free ad.
And it didn’t look like a glitch. It looked injected.
No suspicious apps. No device compromise. The only thing out of the ordinary was that the “share image” Spotify generates had been swapped.
This might sound like a tiny oddity. It isn’t. It’s a signal that a trusted cross-platform media pipeline might be vulnerable.
How Could This Happen?
Below are the most realistic paths, based on how Spotify structures share assets and how Instagram ingests third-party media.
1. Share Asset Injection via a Manipulated Media Endpoint
Spotify doesn’t screenshot your screen; it generates a dynamic image server-side.
If someone gains the ability to override the image URL or the CDN asset associated with that track, they can push their own image into every share attempt.
This could happen through:
- compromised distributor metadata
- misconfigured catalog ingestion
- legacy asset references Spotify still honors
- CDN cache poisoning at the object level
For older catalog tracks (especially pre-Spotify era imports), this is surprisingly plausible.
2. Metadata Poisoning on Legacy Tracks
Tracks published long before streaming often carry messy metadata.
If an attacker slipped in a malformed image, link, or social-share-template fields during a re-upload or distribution update, Spotify’s pipeline might accept it without proper sanitization.
This is classic “trusting legacy fields too much.”
3. Abusing an Old Content Pipeline Still in Production
Spotify imported millions of tracks using tools built years ago. Some of those ingestion paths still exist for label/distributor uploads.
If someone discovered that older pipelines don’t sanitize image fields, they could attach arbitrary assets that propagate to the share layer.
That’s free real estate.
4. A Real-World Vulnerability Test
There’s also a non-zero chance that someone tested whether Spotify’s share-to-Instagram pipeline can be hijacked.
And at least in this one case, it worked.
Why This Is a Security Issue (Not Just a Funny Glitch)
A compromised share flow gives attackers:
- Instant reach every user who shares the song unknowingly spreads the attacker’s content
- Zero friction delivery no warnings, no approvals, no prompts
- Trusted placement Instagram Stories feel “safe”
- Perfect amplification even a tiny percentage of hijacked shares equals thousands of free impressions
And if someone decides to escalate:
- phishing images
- QR codes
- brand impersonation
- fake giveaways
- crypto scams
This becomes a social engineering goldmine.
Technical Breakdown: Where the Weak Link Probably Is
Spotify’s Flow
- User taps Share.
- Spotify generates or fetches a preview asset.
- Spotify sends a structured intent + image to Instagram.
- Instagram imports it into a Story template.
If step 2 is compromised, everything downstream inherits the malicious asset.
Instagram’s Flow
Instagram trusts the media Spotify sends.
There is no verification mechanism for “Is this image really representing this track?”
That trust is the entire vulnerability.
Most Likely Weak Spot
Old catalog entries stored with unusual or malformed metadata that Spotify’s new pipeline still respects.
Something like:
social_share_image_url = https://attackercdn.com/injected.jpg
If Spotify doesn’t validate that URL at generation time, the door is open.
Mitigation Ideas Spotify Should Probably Consider
1. Strict Source Validation
Only allow artwork from verified, whitelisted storage buckets; not arbitrary distributor metadata.
2. Regenerate Legacy Assets
Force all old catalog items to use Spotify-generated assets rather than distributor-provided links.
3. Metadata Sanitization
Reject any metadata fields that point to external URLs unless cryptographically verified.
4. Share Asset Integrity Tokens
Instagram could require integrity metadata (such as a checksum or signature) to verify the asset. This is how you stop silent injection.
Why This Could Go Viral
- Touches Spotify, Instagram, and nostalgia.
- Mixes a weird glitch with a real security implication.
- People love “Look, the share button can be hacked for free ads” stories.
- The exploit path feels clever enough to spark debate.
- It exposes how old metadata quietly exists inside modern platforms.
It’s the perfect weekend Hacker News thread bait.
The Bigger Point
This whole story highlights something we rarely think about:
Modern social features are built on top of legacy metadata nobody has audited in years.
And if someone can hijack the share pipeline of a global music platform with a single track’s metadata…
…we don’t have a bug — we have an attack surface.
P.S. I don’t usually write about this kind of thing, but it felt really good to think about it and write about it. I’d love to hear your thoughts. If you’d like to reach me, you can use the contact form or my LinkedIn profile at https://linkedin.com/in/ercanermis.
Thank you so much for taking the time to read this. I’m so glad you’re here.