Security first because security is so important! When you create an Amazon Web Services account, that account called a root. Root level account has got full access to all resources running in the cloud environment and I totally recommended don’t use your root account to manage the resources.
What should you do to keep your AWS Account secure?
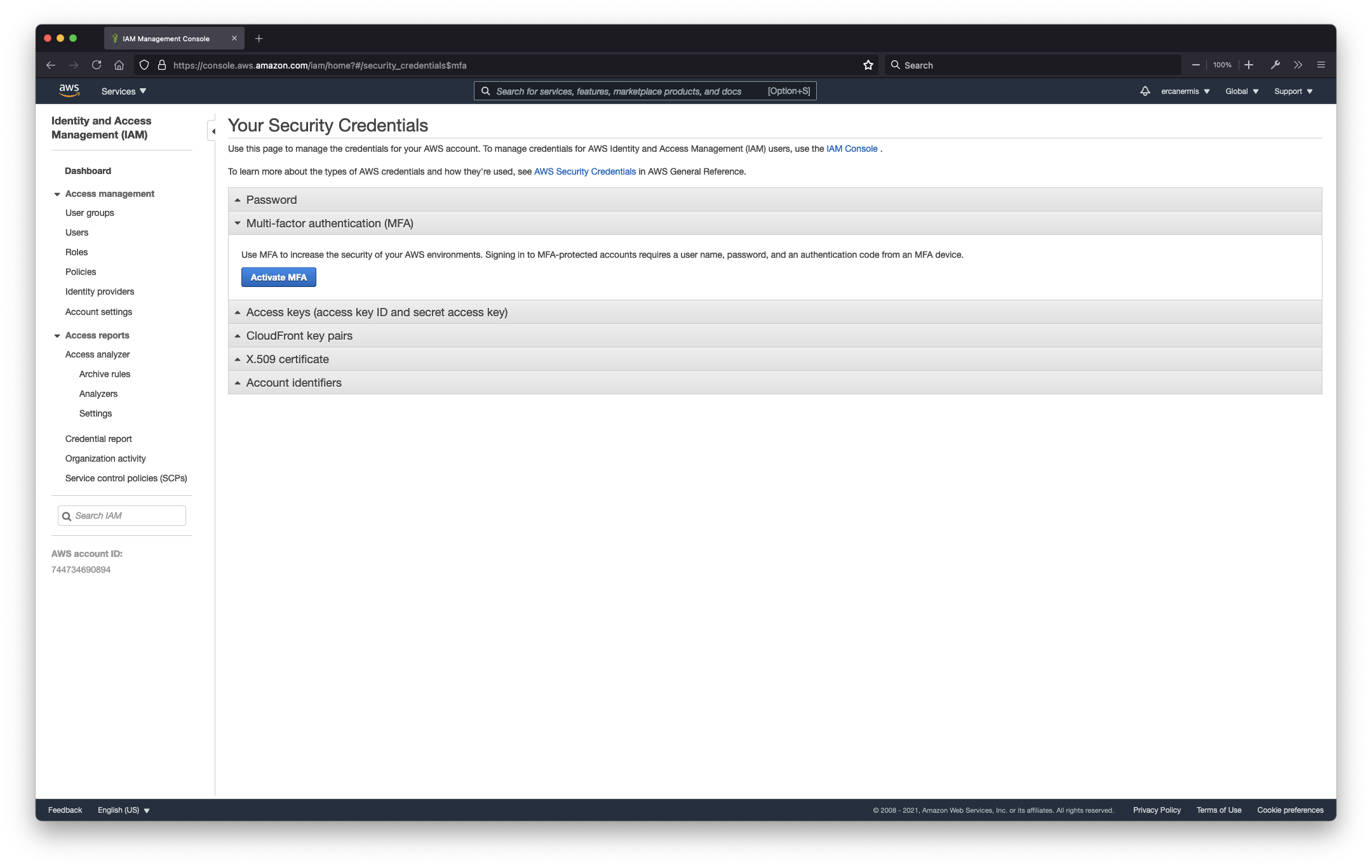
- Set Multi Factor Authentication for root account
Maybe you heard 2 Step Authentication or 2 Factor Authentication previously. In the Amazon ecosystem, we called this extra security layer an MFA. The root user for this account does not have Multi-factor authentication (MFA) enabled. Enable MFA to improve security for this account.
- Set password policy
A password policy is a set of rules that define complexity requirements and mandatory rotation periods for your IAM users’ passwords.
You can set:
– Enforce minimum password length
– Require at least one uppercase letter from Latin alphabet (A-Z)
– Require at least one lowercase letter from Latin alphabet (a-z)
– Require at least one number
– Require at least one non-alphanumeric character (! @ # $ % ^ & * ( ) _ + – = [ ] { } | ‘)
– Enable password expiration
– Password expiration requires administrator reset
– Allow users to change their own password
– Prevent password reuse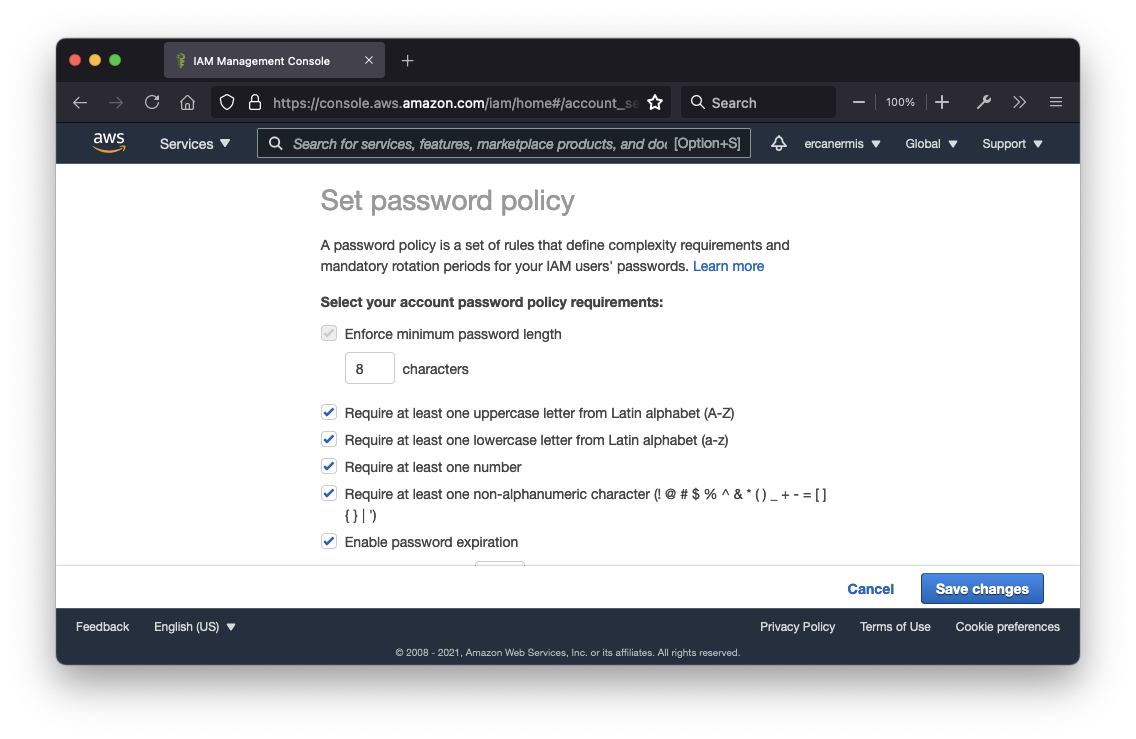
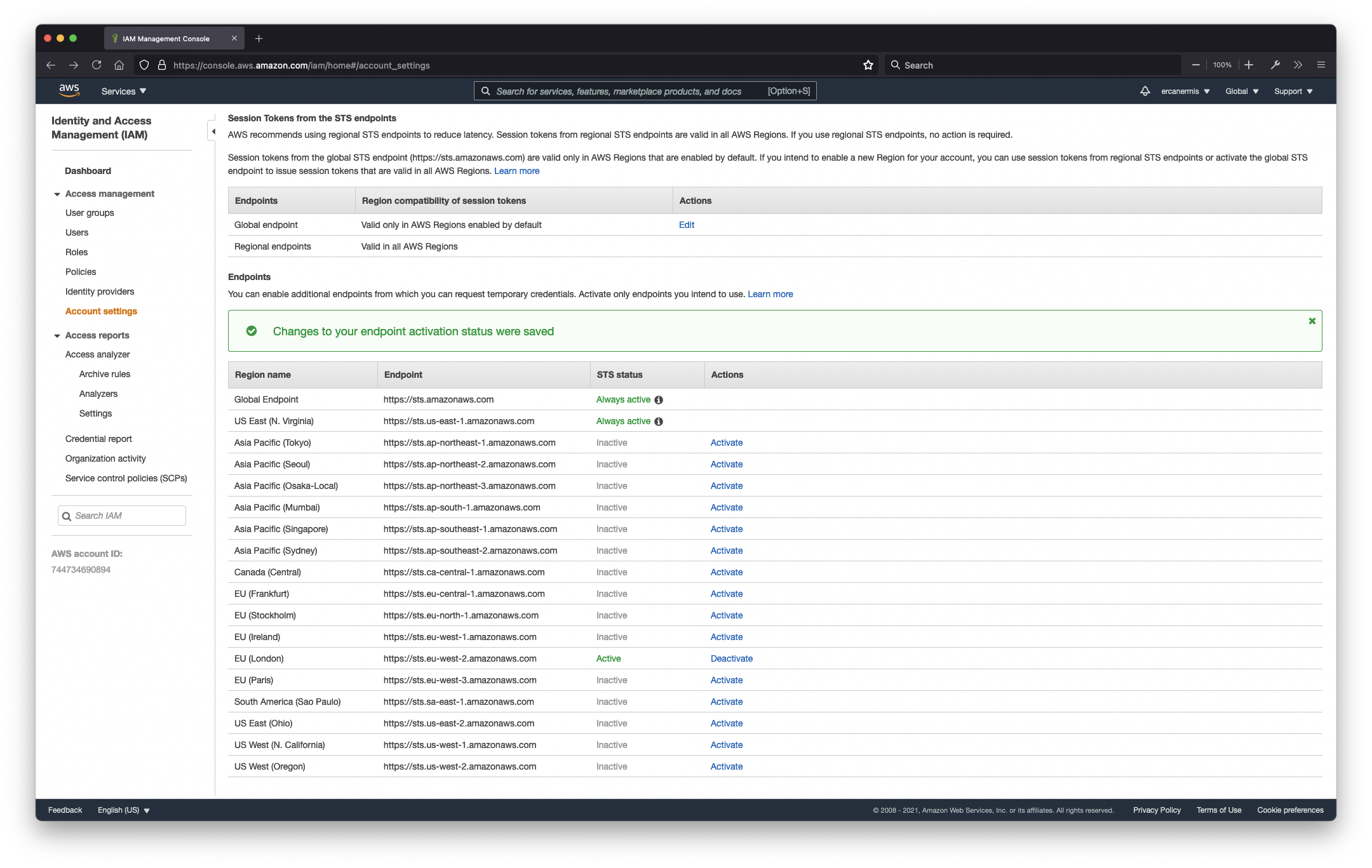
- Deactive Region(s) if you don’t need
In Account Settings, every single region running specifically in Amazon Web Services. For example, if you are planning to run your services in the London region (eu-west-2), actually you don’t need other regions and you should definitely deactivate others. You can’t deactivate Global Endpoint and US East (N. Virginia) regions. The all Amazon Web Services authentication services (such as logins and other service authentications) running in Global Endpoint, some of the services just running in the North Virginia region (us-east-1). That’s the reason you cannot disable them.
- Create Policy
A policy defines the AWS permissions that you can assign to a user, group, or role. You can create and edit a policy in the visual editor and/or using JSON.
You can set specific actions for specific services and resources on create policy page.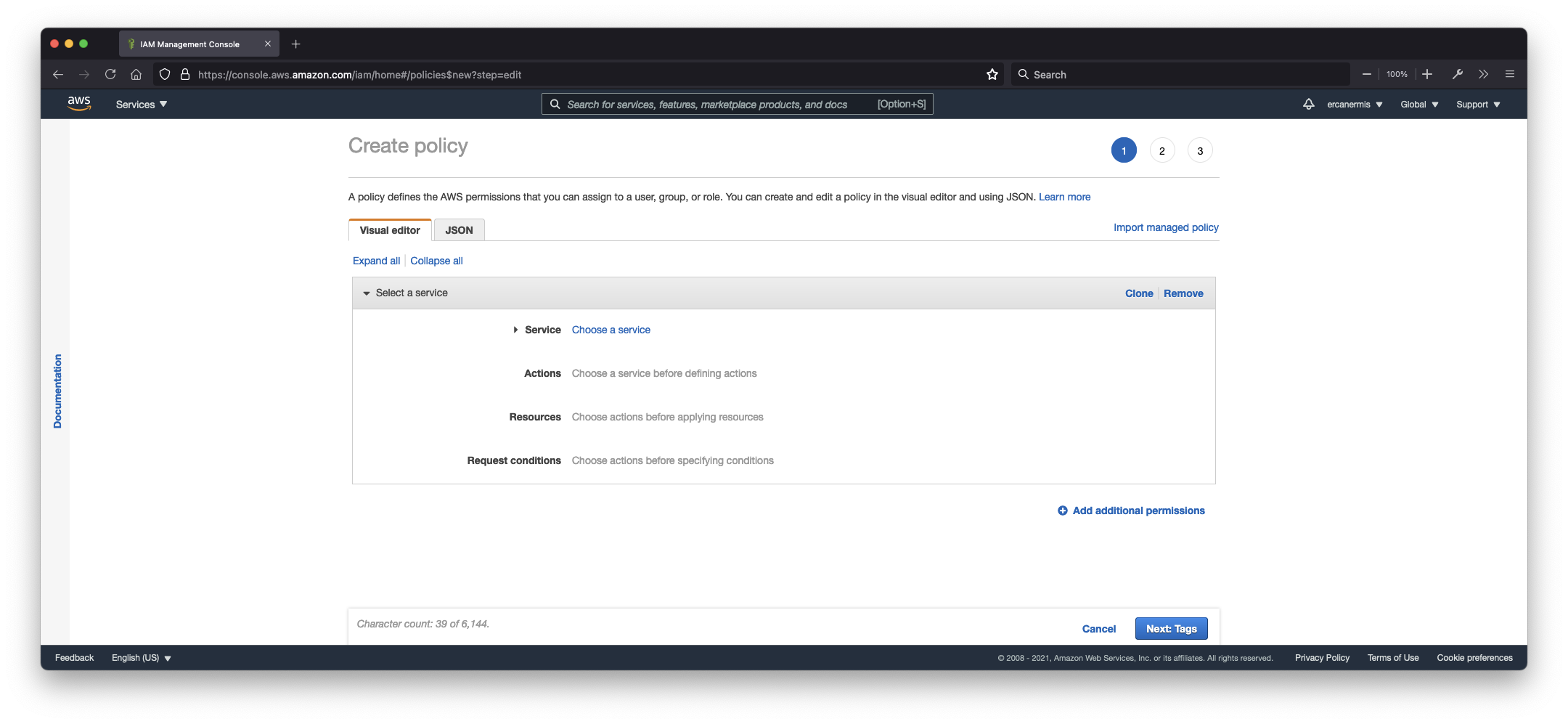
- Create IAM Role
IAM roles are a secure way to grant permissions to entities that you trust. Examples of entities include the following:
– IAM user in another account
– Application code running on an EC2 instance that needs to perform actions on AWS resources
– An AWS service that needs to act on resources in your account to provide its features
– Users from a corporate directory who use identity federation with SAML
– IAM roles issue keys that are valid for short durations, making them a more secure way to grant access.
- Separate your departments with User Groups
An IAM user is an entity that you create in AWS to represent the person or application that uses it to interact with AWS. A user can belong to up to 10 groups. You can attach up to 10 policies to this user group. All the users in this group will have permissions that are defined in the selected policies.
- Apply the best practices
Grant least privilege access: Establishing a principle of least privilege ensures that identities are only permitted to perform the most minimal set of functions necessary to fulfill a specific task while balancing usability and efficiency.
Use AWS Organizations: Centrally manage and govern your environment as you scale your AWS resources. Easily create new AWS accounts, group accounts to organize your workflows, and apply policies to accounts or groups for governance.
Enable Identity federation: Manage users and access across multiple services from your preferred identity source. Using AWS Single Sign-On centrally manages access to multiple AWS accounts and provides users with single sign-on access to all their assigned accounts from one place.
Enable MFA: For extra security, we recommend that you require multi-factor authentication (MFA) for all users.
Rotate credentials regularly: Change your own passwords and access keys regularly, and make sure that all users in your account do as well.
Enable IAM Access Analyzer: Enable IAM Access Analyzer to analyze public, cross-account, and cross-organization access.
Learn more about all security best practices.
I hope, this article will help you to use your Amazon Web Service account securely!